An incident response retainer can play a critical role in transforming how organisations prepare for and respond to cyber incidents.
However, while the retainer model has evolved to meet changing security needs, not all options offer the flexibility required in today’s complex threat landscape.
This article outlines how the incident response retainer has changed and continues to develop in scope, and also looks at the different types of available retainer models.
Changing how incident response is delivered
Widely adopted by organisations, incident response retainers provide a formalised and structured agreement between companies and security services providers. By ensuring that an organisation is able to respond quickly and effectively in the event of a cyber incident, a retainer provides proactive support for protecting its operations, reputation and bottom line.
This model also means that companies can ensure timely response and notification for cyber incidents in compliance with privacy and consumer protection laws. It also removes the risks associated with having to find expert support in the event of a major attack affecting many organisations at the same time.
The evolving nature of the incident response retainer
Historically, incident response relied on a complex and very lengthy process of analysis to understand the events involved in an incident. This meant that it was not suited to being packaged up as part of a discrete service.
As incident response evolved to become more streamlined, the incident response retainer became a valuable security solution. As the name suggests, it was traditionally focused on providing a prepaid package of support for organisations in the event of a security incident. The premise was simple: an organisation would pay in advance for support during an incident and the company they had chosen would provide those services if and when an incident occurred.
However, with more advanced incident response tools such as XDR and EDR providing real-time insight into the status of an organisation’s environment, IR retainers continue to develop to better meet changing security goals and concerns.
Some retainer providers now also offer additional services, beyond the scope of digital forensics and incident response. Unused retainer credits can then be used to procure proactive services like risk assessments and penetration tests.
Understanding your retainer options
While the tech they incorporate has changed, incident response retainers usually still follow one of two common frameworks:
Prepaid: The company pays upfront for a certain number of hours, typically per month or per quarter, which can be used to respond to cyber incidents. This arrangement will be based around a service level agreement (SLA). If the retainer hours are not used in full, they can be spent on other incident response services or incident preparedness services. The challenge with this approach is that there is pressure on the customer to use those up within a specific period.
Zero-cost: The agreement specifies an SLA, the nature of services provided, a procedure for declaring incidents, and a cost per incident. This is paid only if the vendor actually provides services.
Purchasing an incident response retainer
The ways in which organisations can purchase an IR retainer is changing as new approaches emerge:
Working with a third-party incident response vendor
One common approach is for a company to have a contract with a third-party IR vendor. However, even as experts in their field, they won’t have operational knowledge of their customer’s business. Onboarding a third party and providind the necessary insight into your organisation’s systems and security environment can delay key actions at a critical time.
Engaging your cyber insurance provider
Procuring incident response services via your insurance provider can offer the peace of mind of knowing that the company is a trusted incident response vendor. However, because insurers can be cost-sensitive, you need to be clear about exactly what’s being offered in terms of SLAs. Speed and cost may be prioritised over breadth of service, for example.
Customising your incident response retainer
A new evolution in the IR retainer landscape is the emergence of the customisable retainer. This model allows organisations to adapt retainer packages to include a wider range of services, ensuring that they meet their exact needs.
Organisations should keep in mind that legacy IR retainers focus on incident response and forensics only, without the scope to cover broader assistance with breach response, like breach notification, crisis communications or litigation support. Because of this, it is important to be vigilant about selecting a retainer that not only goes beyond incident response, but also provides true flexibility and breadth of service.
Through providers capable of delivering both MDR and breach response, the incident response retainer has now evolved to become an even broader and more cohesive offering. By combining an MDR service with a cyber retainer that can adapt to meet their specific security issues and needs, organisations can achieve true cyber resilience.
Because the MDR provider’s security specialists engage daily with the threats targeting a business, they better understand its security posture and processes. This helps to reduce costs in terms of the hours required to understand a company’s particular environment and relevant threats. It also means that an MDR provider can ensure a seamless transition from the detection of and response to known threats to escalating an unknown, complex incident to their own DFIR team, working in close collaboration with their SOC analysts.
How Kroll can help
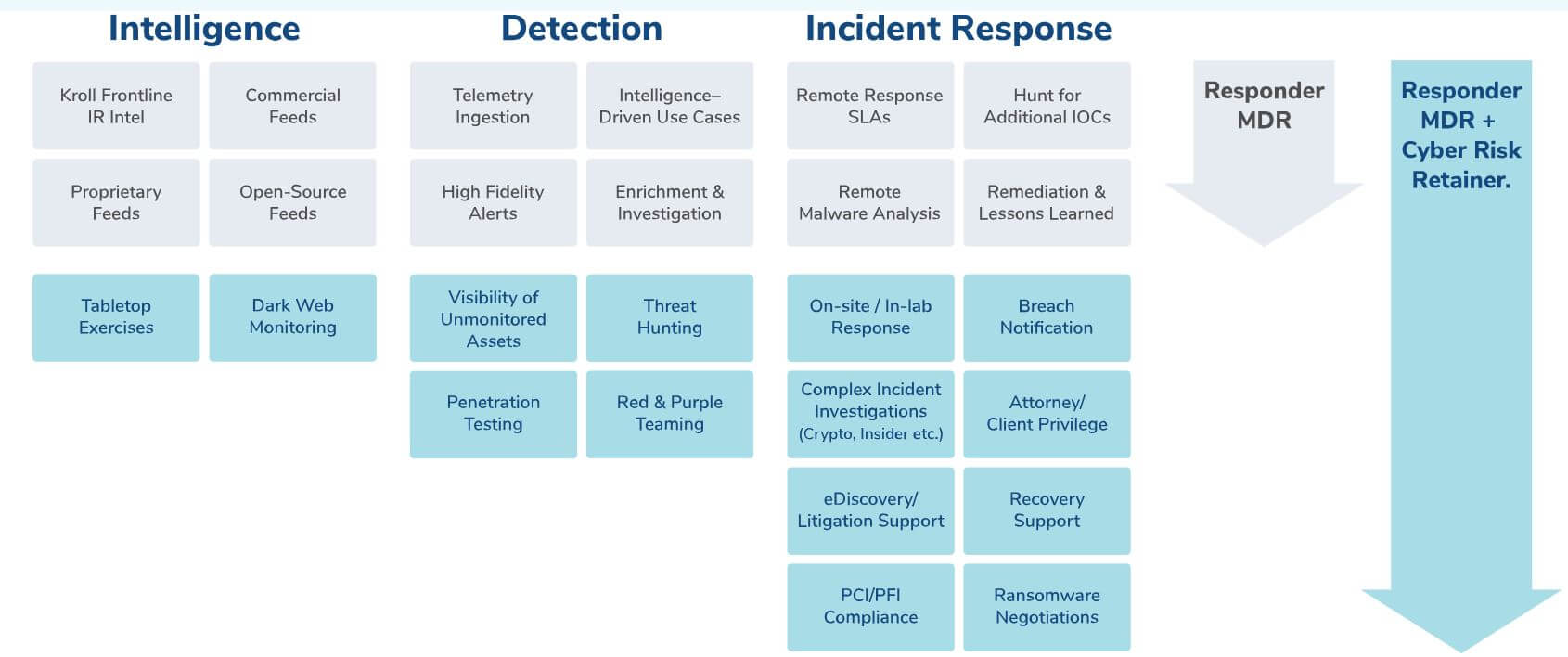
At Kroll, we offer an unrivalled incident response retainer by bringing together elite digital forensics and incident response capabilities with maximum flexibility for proactive response and notification services. A Kroll incident response retainer guarantees expedited response as well as notification and proactive services to minimise the impact of an incident. Our retainer options enable organisations to maximise the value of cyber security investments through a clear service structure.
Unlike other firms, Kroll gives you the opportunity to customise cyber risk retainers with a wide variety of proactive, response and notification services best suited for your situation and goals. This ensures that your organisation benefits from digital forensics, incident response and offensive capabilities on demand. From preparedness services to breach response, Kroll’s services are flexible and configurable to the needs of your environment, regardless of the technologies you use.
Because our cyber risk retainer offers transparent pricing, you benefit from tangible value for your retainer investment and the peace of mind of knowing you can depend on Kroll’s prioritised response and global resources in a crisis.




