A new Kroll report, The Detection and Response Maturity Model, highlights a concerning gap between organisations’ perceptions of their detection maturity status and their actual cybersecurity practices.
The Kroll Detection and Response Maturity Model analyses 1,000+ security programs from organisations around the world to identify their actual maturity, the ROI of mature programs and what security leaders can do to elevate their detection and response capabilities.
The report leverages data uncovered in our The State of Cyber Defense 2023: The False-Positive of Trust, which looked at responses from 1,000 global security decision-makers. By layering those insights with Kroll’s frontline threat intelligence, the report highlights the perceptions and realities of threat detection to develop the Model. The Model will help security leaders to benchmark their programs, prioritise investments and increase their cyber resilience.
View the Interactive Detection and Response Maturity Curve
Informed by our findings, we have developed an interactive model to enable organisations to explore how revenue, region and key industries fall within the maturity curve. View the model now.
Three key maturity categories
Our framework is made up of three categories: Novice, Explorer and Trailblazer. Novices have low cyber maturity, Explorers show average maturity and Trailblazers demonstrate the highest level of maturity.
| Novice | Explorer | Trailblazer |
|---|---|---|
| They are likely to be using simpler collection and monitoring tools to detect cyberattacks and may not have any actions for responding to high-severity threats or use threat monitoring and investigation as their only defenses. They only have a few elements in their cybersecurity program. | They may have access to limited threat intelligence and can create some custom use cases/rules to alert them of known cyberattacks and use multiple tools to detect high-severity threats. They have multiple elements in their cybersecurity program. | They are likely leveraging various sources of threat intelligence to continuously improve detection rules, proactively hunt for unknown threats, or detect them in real-time. They have many actions to respond to high-severity threats, including remediation and forensics, and likely have a large cybersecurity toolkit. |
The critical gap between perception and reality
Our findings highlight a considerable difference between businesses that think they are cyber mature compared to those that actually are. Organisations in the Trailblazer group are less likely to report that they are “very mature” (13%), in comparison with Explorer or Novice organisations. Plus, 43% of those placed in the Novice group feel that their detection and response measures are very mature with no improvement required.
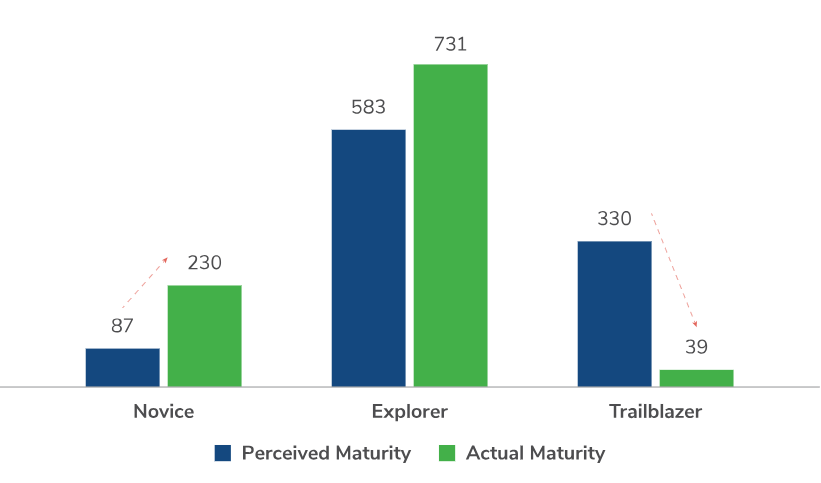
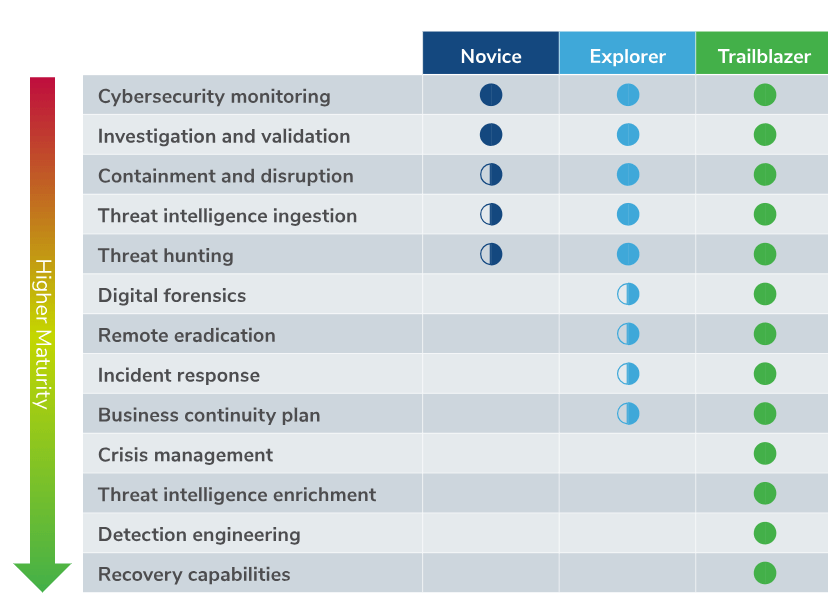
Organisations are missing key threat detection and response capabilities
A robust detection and response strategy is made up of the following elements, listed from most basic to most advanced.
Just 3% of organisations’ cybersecurity programs include all the threat detection and response elements required to support full maturity. Worryingly, 20% of businesses only have the basic cybersecurity monitoring with no further processes in place.
Organisations self-reporting as having a high level of cyber maturity are also more likely to only have cybersecurity monitoring in place. This further illustrates the disparity between what business think is true cyber maturity and actual cyber maturity.
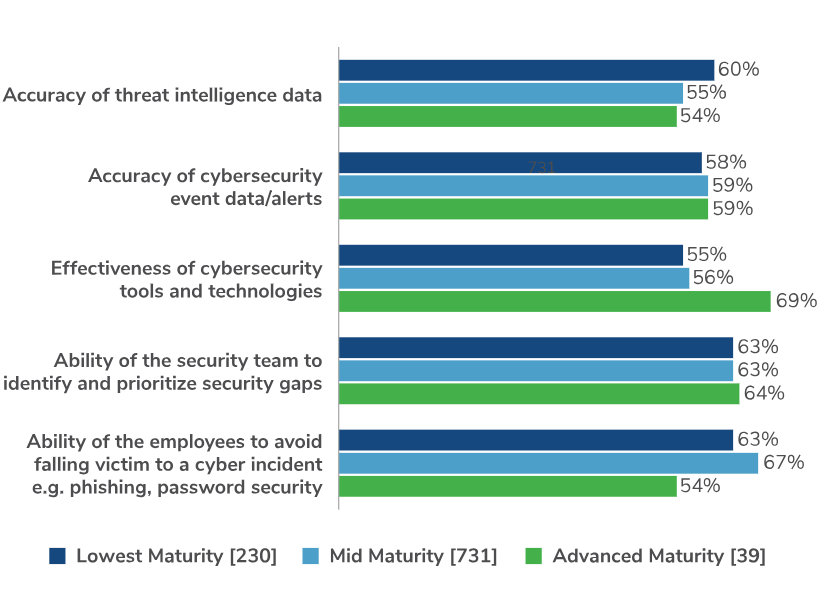
Trailblazers trust security tools the most, but humans are key to avoiding threats
In the Kroll report The State of Cyber Defense 2023: The False-Positive of Trust, we showed that security teams generally trust employees to avoid falling victim to a cyberattack above the accuracy of cybersecurity alerts and the effectiveness of security tools. However, when looking at the data through the lens of cyber maturity, the statistics are reversed. For Trailblazers, employees are trusted the least (54%) and the effectiveness of cybersecurity tools is trusted the most (69%).
Learn more
The full report covers:
- How to overcome challenges caused by discrepancies between perceived and actual maturity
- The ROI of detection and response maturity
- The threat detection and response capabilities missing from many organisations’ strategies (including cyber insurance)




