Kroll’s latest threat landscape report reveals fragmented threat actor groups and a continued evolution in attack methods and approaches.
These, as well as other notable trends from the previous quarter, are discussed in the report, Q1 2023 Threat Landscape Report: Ransomware Groups Splinter, Swarm Professional Services.
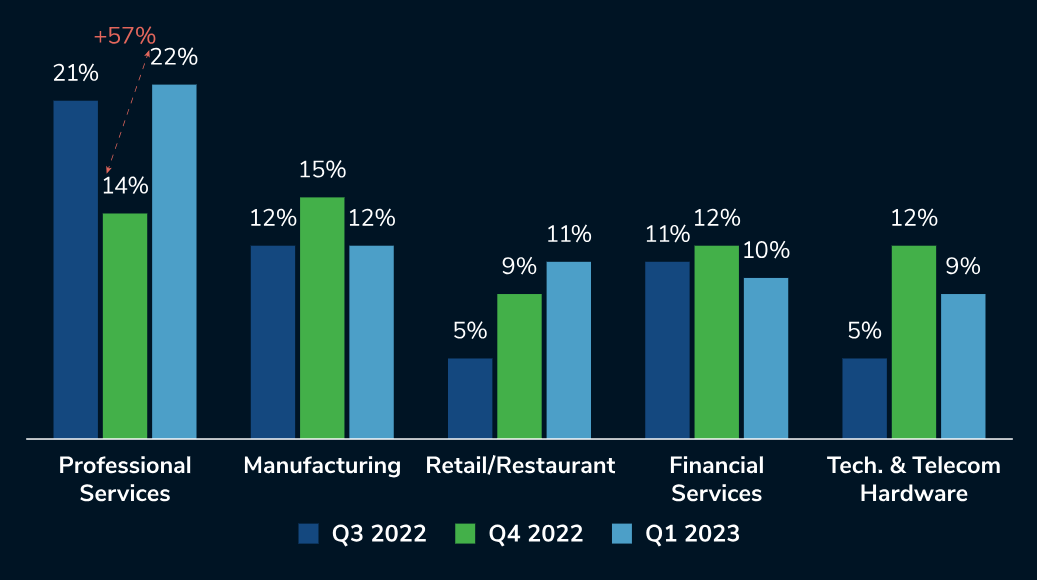
Sharp rise in targeting of professional services
In Q1 2023, Kroll observed a 57% increase in the overall targeting of the professional services sector from the end of 2022. Ransomware propelled this increase as organisations within the sector, particularly legal firms, were the most likely target of extortion and encryption attacks in Q1 2023.
Overall, ransomware accounted for 30% of Q1 cases and 26% of email compromise cases, both remaining closely aligned with the 2022 levels. In Q1, Kroll noted a 56% increase in the number of unique ransomware variants observed.
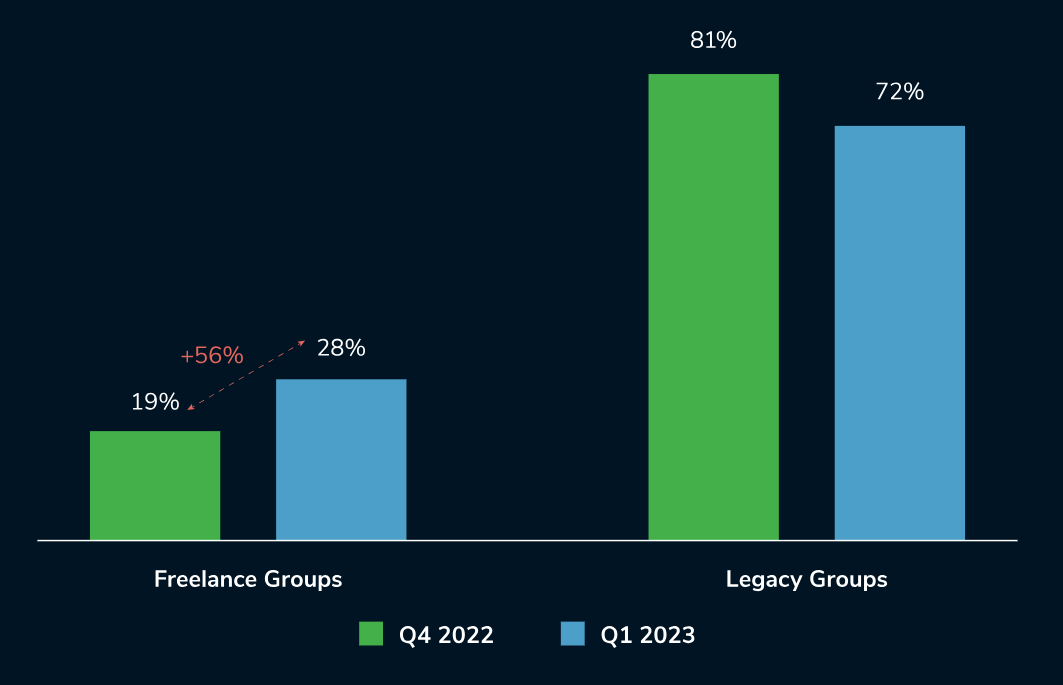
While well-known ransomware-as-a-service (RaaS) operations such as LOCKBIT continue to dominate the ransomware landscape, Kroll observed a number of lesser-known variants during the quarter.
Some of these were new but others were established groups that had not been observed for several quarters. The rise in these lesser-known variants, such as XORIST, highlights the number of independent attackers conducting ransomware operations outside of the established RaaS groups.
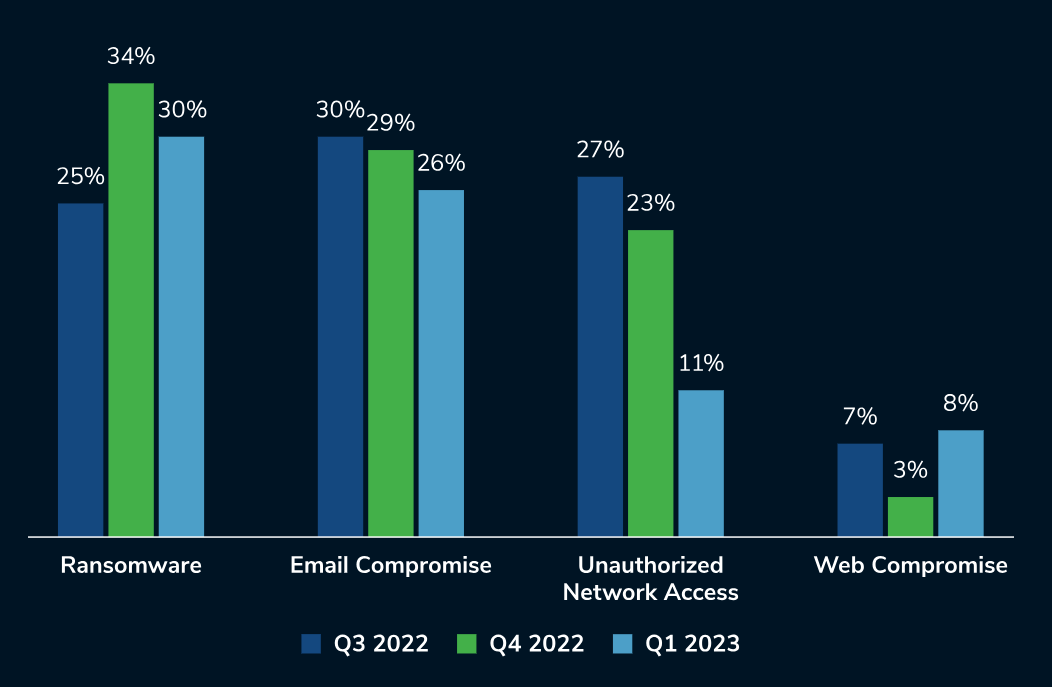
Threat incident types
Kroll observed that ransomware and email compromise continue to be the most impactful threats against organisations. Kroll also noted a rise in web compromise, most typically against the retail sector, highlighting that threat actors attack for financial gain.
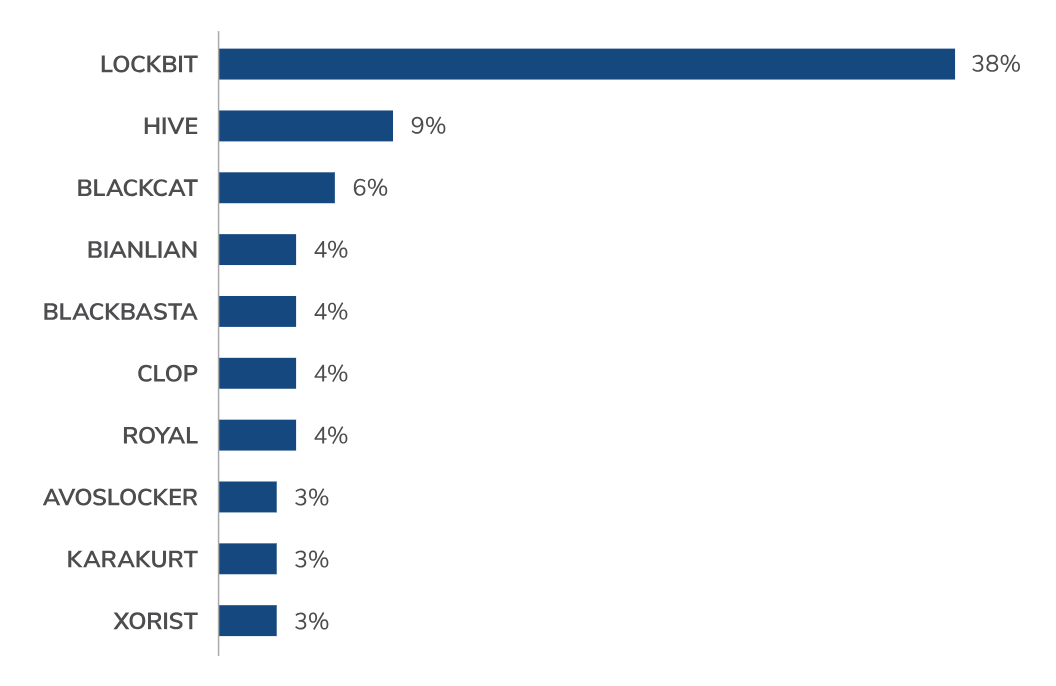
The rise of independent ransomware attackers
Although large RaaS operations such as LOCKBIT dominated the ransomware landscape in Q1, Kroll also observed a 56% increase in unique variants from the previous quarter. This rise in unique variants included new variants such as CACTUS, DARKSKY and NOKOYAWA, and others familiar, but not observed in several quarters, such as XORIST and RANSRECOVERY. Kroll has identified an increase in “one-off” ransomware variants that tend to use well-known builders.
Challenges likely ahead for the rest of 2023
Power shifts among RaaS groups have led to the emergence of lone “splinter” actors that, despite not yet possessing the scope or scale of established groups, are certainly capable of inflicting extensive damage in order to achieve their aims.
Although the professional services sector was the key focus for independent ransomware threat actors in Q1 2023, it is quite possible that other sectors will be targeted in the months to come. To counter these risks, organisations need to be ready to continually review and strengthen their stance to cyber security through threat intelligence and an effective Managed Detection and Response programme.




