A new report from Kroll reveals a concerning trend of threat actors targeting email for access and extortion.
This, as well as other notable threats from the previous quarter, are discussed in the report, Q1 2022 Threat Landscape: Threat Actors Target Email for Access and Extortion.
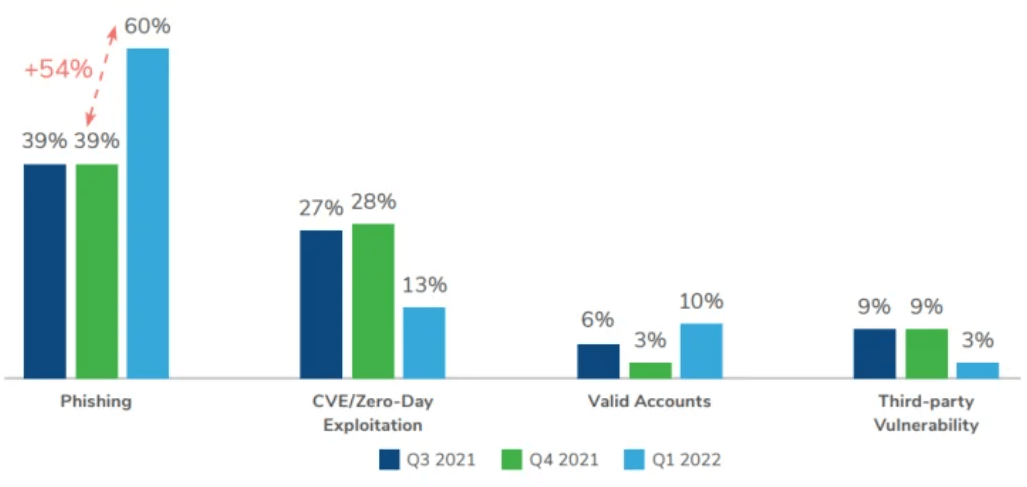
Incidences of phishing for initial access soar
In Q1 2022, Kroll observed a 54% increase in phishing attacks being used for initial access in comparison with Q4 2021. Email compromise and ransomware were the two most common threat incident types, highlighting the integral part played by end users in the intrusion lifecycle.
Well-known vulnerabilities used as pivot points to access and compromise systems
The report highlights that Kroll continues to observe widely-publicised vulnerabilities such as ProxyShell and Log4J being used as pivot points for attackers to access and compromise systems through approaches such as business email compromise and cryptominers. In Q1 2022, Kroll observed these vulnerabilities being leveraged by multiple different ransomware groups for initial access into systems. In the same quarter, Kroll also observed an increase in attacks related to Emotet and IcedID malware.
Email compromise rises while ransomware ebbs
The report discusses that while email compromise saw an increase of 19% from Q4, ransomware incidents trended down. Overall, ransomware activity in the first quarter of 2022 was down nearly 30% from Q3 2021. Kroll observed an uptick in ransomware activity in March 2022, indicating the regrouping and rebranding of ransomware gangs as new variants like QuantumLocker and Dark Angel. Web compromise continues to experience a gradual rise as significant vulnerabilities like Log4J and Spring4Shell make it easier for cybercriminals to exploit web applications.
Email compromise leads to extortion
The report outlines a case study that is of particular interest because it illustrates the ongoing trend of email compromises followed by attempts to financially extort individuals or organisations, reflecting the tactics employed by ransomware gangs. The case study begins with a phishing email targeting IT departments and ends with the threat actors using multiple different methods to contact the compromised account holders and even taking over social media accounts associated with the employees to further pressure victims into meeting their ransom demands.
Defending against established methods and new approaches
The report shares key insights that confirm that even with fewer ransomware incidents and the disruption and exposure of a number of key threat groups, the threat landscape remains complex. With attacker diversity at the fore, due to actors exploiting new methods and the ongoing events relating to Russia’s war on Ukraine, it is highly likely that conditions will remain challenging throughout 2022.
It is essential to maintain a robust cyber security approach in order to defend against the ongoing acceleration of cyber threats throughout the second half of 2022. Apart from outlining email security best practices, the report also demonstrates the value of threat intelligence and the importance of an effective Managed Detection and Response programme.




